“To catch a hacker, think like one—then protect others before the bad guys get there first.”
In today’s hyper-connected world, cyberattacks are growing both in number and sophistication. That’s why understanding the ethical hacking lifecycle is more important than ever. This systematic process helps organizations stay ahead of malicious hackers by identifying vulnerabilities before they become actual threats.
Think of it as hiring a professional to break into your digital home—not to steal anything, but to find out where the locks are weak.
Whether you’re a student, aspiring ethical hacker, IT professional, or business owner, this comprehensive guide will help you understand the ethical hacking stages in plain, everyday language.
- 🔄 Understanding the Ethical Hacking Stages
- ✅ Why the Ethical Hacking Lifecycle is a Must-Have Framework
- 🔍 1. Reconnaissance – The First Phase of the Hacking Process
- 🧭 2. Scanning – Mapping the System in the Phases of Ethical Hacking
- 🔓 3. Gaining Access – The Heart of the Hacking Processing
- 🔐 4. Maintaining Access – A Core Principle of the Ethical Hacking Methodology
- 🧽 5. Clearing Tracks – Final Step in the 6 Phases of Ethical Hacking
- 📋 6. Reporting & Remediation – Often Overlooked in the Types of Ethical Hacking
- 🔄 7. Retesting – Crucial Step in the 7 Steps of Ethical Hacking
- 🧠 Bonus: Different Types of Ethical Hacking Explained
- 🔗 Want to Learn More?
- 📚 Frequently Asked Questions (FAQ)
🔄 Understanding the Ethical Hacking Stages
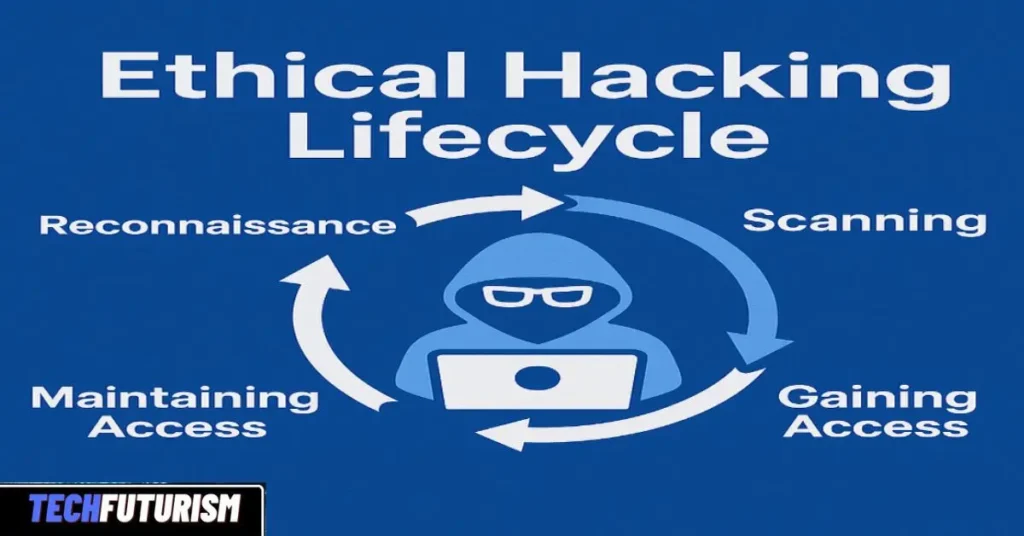
The ethical hacking lifecycle in cyber security is typically divided into structured phases. Though some models mention 5 or 6 steps, the industry standard tends to follow the 7 steps of ethical hacking.
Let’s walk through each stage of the process to understand how it works and why it matters.
✅ Why the Ethical Hacking Lifecycle is a Must-Have Framework
In today’s digital battlefield, the best offense is a well-tested defense. The ethical hacking lifecycle helps companies expose weak points before attackers do. It turns security into a proactive process, not just a reaction to incidents.
🔁 Recap of the Lifecycle:
| Phase | Purpose |
| Reconnaissance | Discover public-facing information |
| Scanning | Analyze systems and vulnerabilities |
| Gaining Access | Simulate real-world attacks |
| Maintaining Access | Test persistence methods |
| Clearing Tracks | Assess detection and recovery ability |
| Reporting | Document findings and fixes |
| Retesting | Ensure problems are solved |
By following the ethical hacking lifecycle, you’re not just fixing flaws—you’re fortifying trust, protecting your brand, and keeping your customers safe.
🔍 1. Reconnaissance – The First Phase of the Hacking Process
The first step is reconnaissance, or simply put, researching the target. Ethical hackers collect as much information as they can—think IP addresses, email domains, DNS records, employee names, and even job postings.
This phase is broken down into two parts:
- Passive Reconnaissance: Observing the target without interacting (e.g., using search engines or public data).
- Active Reconnaissance: Interacting directly, such as pinging the target or using network tools.
Common tools:
- Maltego
- Recon-ng
- Google Dorking
Anecdote: One ethical hacker discovered the organizational chart of a tech firm just by scanning public LinkedIn profiles of its employees.
🧭 2. Scanning – Mapping the System in the Phases of Ethical Hacking
With data collected, the hacker uses scanning techniques to learn more about the network. The goal? To find weaknesses—open ports, running services, firewall configurations—that can be exploited later.
Scanning techniques include:
- Port Scanning (to identify open ports)
- Network Mapping (to chart connected devices)
- Vulnerability Scanning (to detect known security flaws)
Tools used:
Pro Tip: This phase is like peeking through the digital windows of your home—what’s visible from the outside?
🔓 3. Gaining Access – The Heart of the Hacking Processing
Now it’s time to exploit the identified vulnerabilities. In the gaining access phase, ethical hackers attempt to infiltrate systems—just like real attackers would.
Methods may include:
- Phishing attacks
- Brute-force attacks
- Payload delivery using tools like Metasploit
Anecdote: An ethical hacker spoofed a CTO’s email and sent a fake HR onboarding document embedded with a reverse shell. It worked. They gained system access within 20 minutes.
🔐 4. Maintaining Access – A Core Principle of the Ethical Hacking Methodology
Once inside, the ethical hacker tests how long they can stay undetected. This helps organizations evaluate their ability to monitor, detect, and block intruders in real-time.
Techniques used:
- Creating stealth admin accounts
- Installing backdoors or Trojans
- Establishing reverse shells for remote control
Case Study: A tester once created a dummy admin account named similarly to existing ones—so well-disguised it went unnoticed for days.
🧽 5. Clearing Tracks – Final Step in the 6 Phases of Ethical Hacking
After the test, the hacker ensures their tracks are wiped clean to simulate real-world attack stealth. This step helps gauge how effective the organization’s log management and intrusion detection systems are.
Actions include:
- Deleting command history
- Clearing logs and temp files
- Removing fake user accounts
Important: Ethical hackers usually operate behind VPNs and use MAC address spoofing to mask their identity throughout the process.
📋 6. Reporting & Remediation – Often Overlooked in the Types of Ethical Hacking
A detailed report is created, outlining everything from vulnerabilities discovered to methods used and fixes recommended. This is where ethical hacking becomes truly constructive.
Reports often include:
- Screenshots of exploits
- Vulnerability scores
- Fixes and best practices
Pro Tip: Good hackers don’t just point out problems—they guide you to fix them.
🔄 7. Retesting – Crucial Step in the 7 Steps of Ethical Hacking
Once fixes are applied, it’s essential to retest to verify whether the vulnerabilities have been properly patched. This feedback loop ensures long-term cybersecurity resilience.
Advice: Make retesting a quarterly habit or after every major system update.
To really understand each step in the ethical hacking process, it’s helpful to first know how computer hacking works in general.
🧠 Bonus: Different Types of Ethical Hacking Explained
Understanding various types of ethical hacking can help organizations tailor their security efforts:
| Type of Hacking | Description |
| Web Application Hacking | Tests websites and portals for vulnerabilities |
| Network Hacking | Assesses internal/external network security |
| Wireless Hacking | Focuses on Wi-Fi protocols and encryption |
| Social Engineering | Exploits human error through manipulation |
| Cloud Security Testing | Analyzes cloud setups like AWS, Azure, GCP |
Explore more at GeeksforGeeks – Types of Ethical Hacking
🔗 Want to Learn More?
Here are some valuable resources to deepen your knowledge:
- Certified Ethical Hacker (CEH)
- Kali Linux Tools List
- Cybersecurity for Beginners – Coursera
- TryHackMe Labs
- Hack The Box Platform
- NIST Cybersecurity Framework
Ready to strengthen your digital defenses?
Invest in ethical hacking services or train your in-house security team today to stay ahead of threats with confidence. With the right process and skilled testers, the ethical hacking lifecycle becomes your greatest cybersecurity asset.
📚 Frequently Asked Questions (FAQ)
❓ What are the 5 stages of ethical hacking?
The 5 stages of ethical hacking are a simplified version of the full ethical hacking lifecycle. These stages help ethical hackers simulate real-world cyberattacks in a controlled way to find and fix system weaknesses before malicious hackers do.
Here’s a breakdown of the five core stages:
Reconnaissance – The hacker gathers info about the target (like domain names, IP addresses, and employee details) without interacting much with the systems.
Scanning – Tools are used to find open ports, active devices, or services that could be vulnerable.
Gaining Access – The hacker tries to exploit a vulnerability (like a weak password or unpatched software) to get into the system.
Maintaining Access – Once inside, the hacker sees if they can stay hidden and keep access for longer periods without being detected.
Clearing Tracks – The hacker removes evidence of the attack by deleting logs or hiding their activity to simulate a real, stealthy attack.
These steps help security professionals identify how a system might be breached—and how to stop it before it happens.
❓ What is the life cycle of hacking?
The life cycle of hacking, also known as the ethical hacking lifecycle, refers to the step-by-step process that ethical hackers use to test and secure a computer system. This method is used to find security gaps and help organizations protect their data and digital assets.
Think of it like a digital safety inspection. The hacker mimics what a real attacker might do but in a safe and legal way. The typical hacking lifecycle includes:
Reconnaissance (research)
Scanning (finding weaknesses)
Gaining access (trying to break in)
Maintaining access (staying connected)
Clearing tracks (covering their trail)
Reporting (sharing what was found)
Retesting (making sure issues are fixed)
This full cycle gives companies a realistic view of how vulnerable their systems are and how to fix those weak spots.
❓ What is the ethical hacker cycle?
The ethical hacker cycle is just another name for the ethical hacking lifecycle. It’s a structured process that ethical hackers follow to assess the security of a system, find loopholes, and recommend solutions.
This cycle usually includes these key steps:
Information Gathering – Also called reconnaissance, where the hacker learns about the target.
Scanning & Enumeration – The hacker uses tools to discover open ports, services, and system details.
Exploitation – Attempting to break into the system using discovered weaknesses.
Post-Exploitation – Seeing how deep the access goes and how long it can be maintained.
Reporting – Sharing detailed results with recommendations to fix the issues.
This cycle is used by cybersecurity professionals, penetration testers, and white-hat hackers to protect systems from real-world threats.
❓ What are the 5 phases of cybersecurity?
The 5 phases of cybersecurity help organizations create a well-rounded security strategy. These phases are about more than just ethical hacking—they cover all areas of cyber protection, from planning to responding.
Here’s a simple breakdown:
Identify – Understand what data, systems, and assets need protection.
Protect – Set up safeguards like firewalls, encryption, access controls, and antivirus software.
Detect – Monitor for unusual activity or intrusions in real time.
Respond – Act fast to contain a threat and reduce the damage when an attack happens.
Recover – Fix affected systems and restore normal operations.
These phases are part of the NIST Cybersecurity Framework and are used by companies around the world to guide their security efforts.